Recovering files after ransomware viruses
There are many encryption viruses in nature. Each one implements its own approach to corrupting user data, acting according to its own script. And due to the fact that the volume of user data is often quite large, and the virus needs to act quickly in order to have time to damage more, without burdening the system and without taking up resources, there are opportunities to restore information «with little blood». That is, it is not always necessary to try to pay extortionists, and often in our laboratory we manage to solve the problem and return undamaged files to users without thousands of dollars of ransom to fraudsters.
A customer contacted our laboratory whose disk was infected with a virus-encryptor, as a result of which all files in several non-system directories, such as «Photos» and «Study» began to look like this:
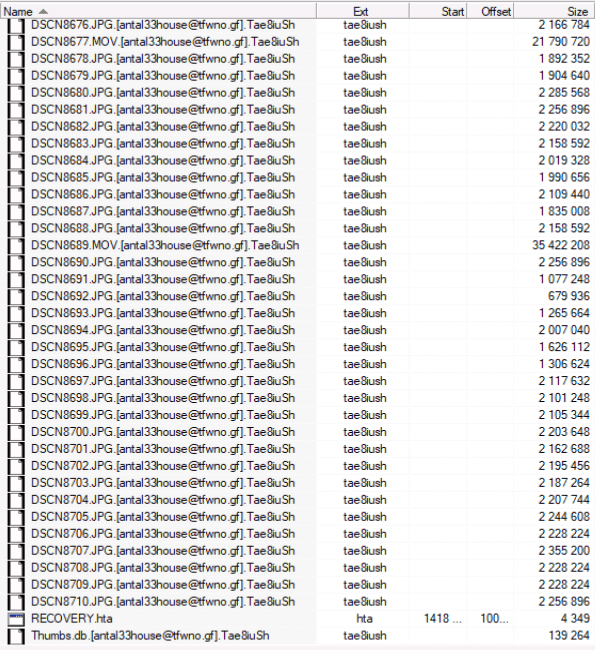
With the extension «tae8iush». By the way, the extension can be arbitrarily different. File «RECOVERY.hta», with a ransom demand to the attackers, is executable, automatically run through the application mshta.exe (Microsoft HTML Application Host) and contains the HTML code, styled, base64 gif and text:
All your files have been encrypted due to a security issue with your PC.
If you would like to restore them, email us at antal33house@tfwno.gf
Also write to us at our backup email: antal33house@dnmx.org
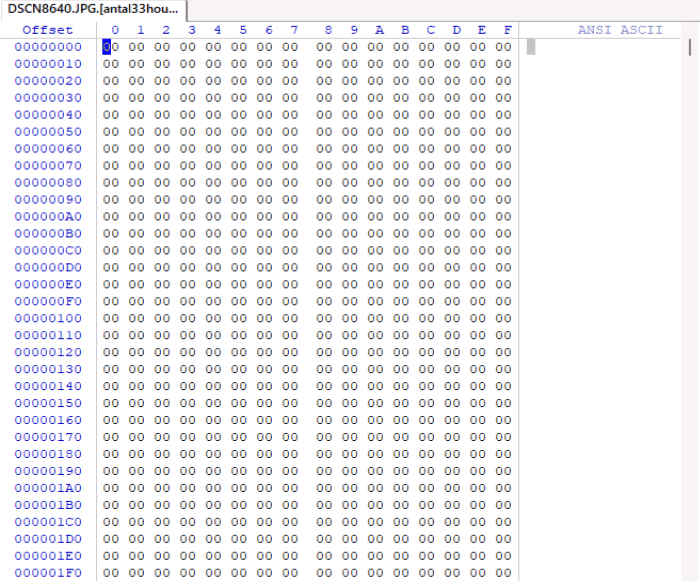
A quick study of the issue revealed that when a file is uploaded to a third-party medium, the resulting file has the expected size, but the contents of the 00h:
By analyzing the MFT records, it was possible to identify the reason for this file content:
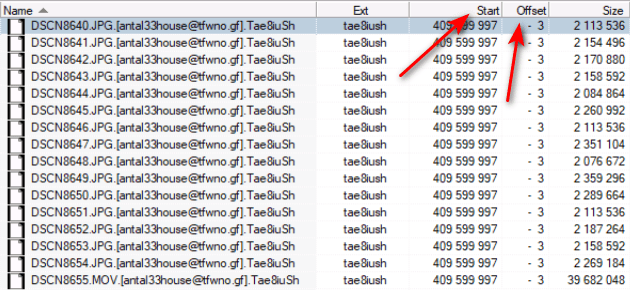
As you can see, all MFT records of «infected» files refer to the same arbitrary LBA address, with the only difference being the size of the addressable area. And, by the way, if this very 409,599,997 LBA address contained any data, such as video, there would be «white noise» instead of zeros, which looks like encryption. Looking at the records themselves localized the problem and gave an insight into the virus algorithm:
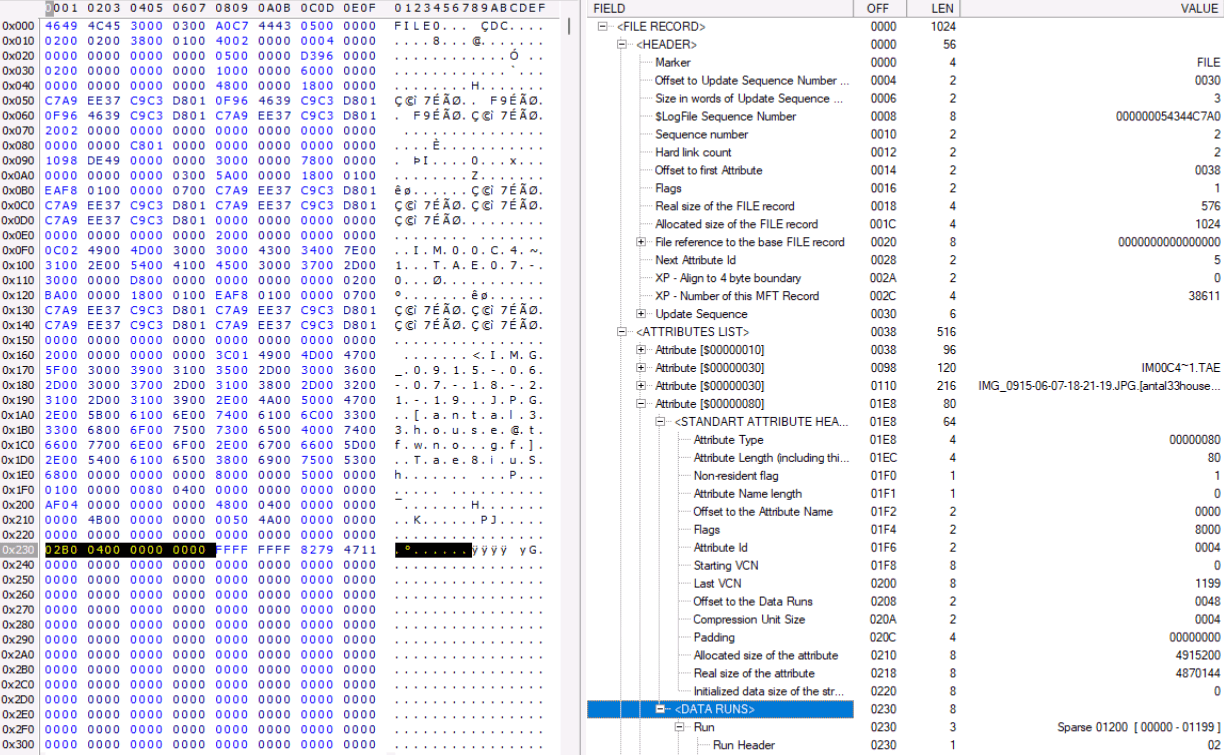
The «encryption virus», or more correctly in this particular case called «ransomware virus», did not actually encrypt the files, but modified the MFT records in the DATA RUNS area - Run Header and Clusters length. And modified the file name and extension, additionally. In order to get back the files needed by the user, we offered two solutions: cheaper and faster, and more expensive and longer.
The first option is to create a logical abstraction using the algorithm «All sectors occupied based on bitmap analysis, minus sectors occupied by unmodified files», with further analysis of the obtained abstraction by finding known file signatures. So called RAW, or «RAW recovery». But not the usual one, but with integrity control of supported file types. As a result of this type of work, the recovery of files infected by the encryption virus is obtained without the directory structure and original file names.
The second option is to create a sector-by-sector copy of the disk, write and debug an executable script to 010Editor on this copy, which will perform reverse modification of MFT records, resulting in full recovery of files infected by the ransomware virus, with original names and structure of folders and subfolders.
Recovering files after an encryptor virus BlackBit
In our Lab customer sent an SSD disk that was infected with a virus. «Black Bit». It's classic, changing file names and extensions to something like this «[WoundedOwl@onionmail.org][SystemID]FileName.BlackBit», ominous messages like:
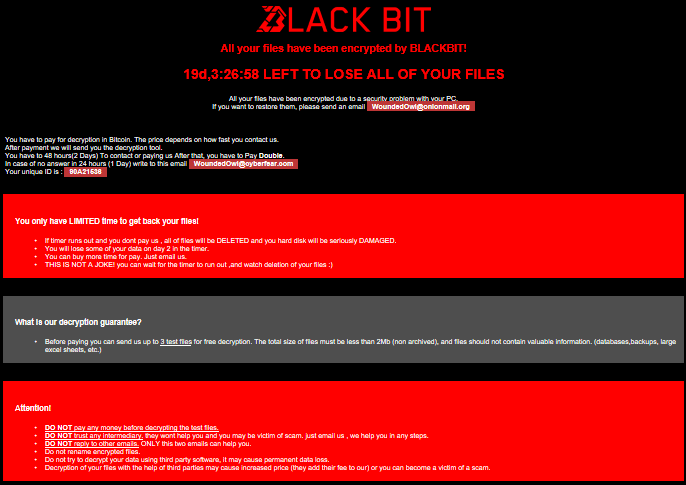
Replacing the volume label with «Locked by BlackBit»:
And in each folder is a file named «Restore-My-Files.txt» and content:
!!!All of your files are encrypted!!!
To decrypt them send e-mail to this address: WoundedOwl@onionmail.org
You can also contact us in Telegram: @WoundedOwl
In case of no answer in 24h, send e-mail to this address: WoundedOwl@cyberfear.com
All your files will be lost on DATE.
Do not go to recovery companies or contact third parties, they are just middlemen who will make money off you and cheat you.
They secretly negotiate with us, buy decryption software and will sell it to you many times more expensive or they will simply scam you.
Your SYSTEM ID : ХХХХХХХ
After reading such outrageous insinuations, my reaction could only be one:

Having received payment for the preliminary analysis from the customer, I started to study the issue. In this case, the file location table had not been changed, except for the renaming of files and their extensions. The first sectors of the files represent «white noise» typical for encryption or other modifications like XOR masking.
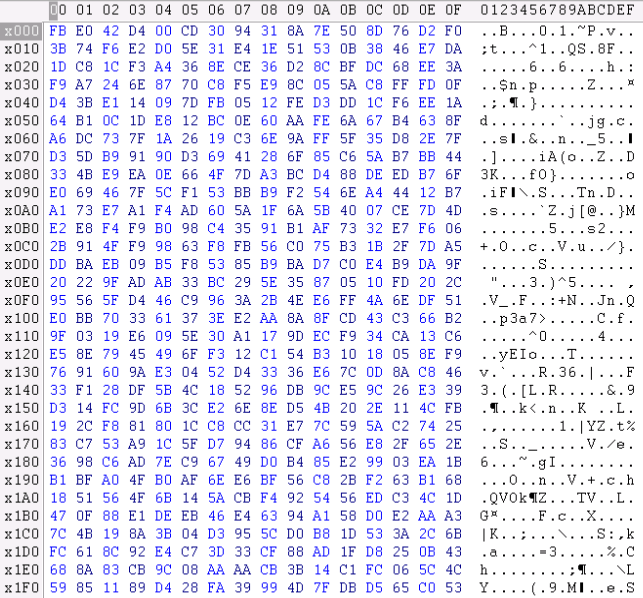
However, next we found out an interesting thing. All more or less large files were modified not completely, but only at 0x00040000h offset, which equals 512 sectors of 512 bytes each. On the example of an XML log file, the boundary is perfectly visible visually.
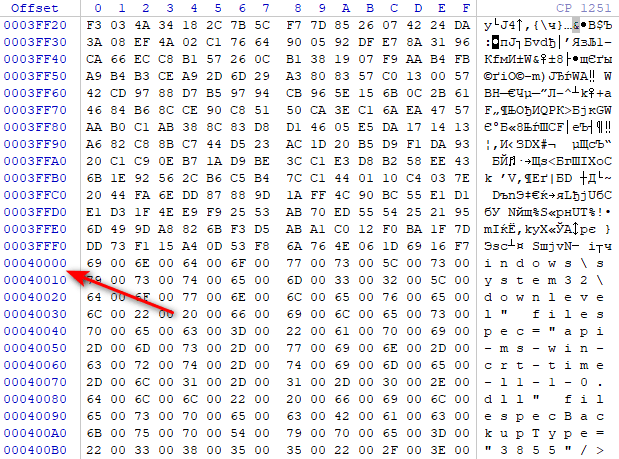
Further study of the data structure in the metafile area revealed the presence of a curious file «Cpriv.BlackBit»:
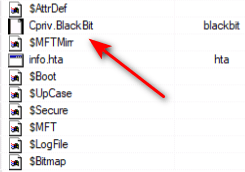
With contents unique to the disk volume, which looks like a public key but is actually an XOR mask that is applied to a sector to emulate its encryption:
At this stage, the virus algorithm became clear and the solution to the problem became clear. When infected, the virus places a file with a xor-mask in the root of the disk, which is overlaid on the first 512 sectors of the files for the virus to work quickly, renaming them and placing a file with a ransom demand in each directory.
Since the customer urgently needed to restore the 1C database file damaged by the encryption virus, the whole work on the restoration of accounting took a few minutes and consisted in renaming the file «1Cv8.1CD» and replacing its damaged header with an undamaged one taken from the old backup.
It took much longer to recover the rest of the files. The first thing was to make a complete clone of the disk and all further work was done on this copy. Next, a script was written that unpacks the initial sectors and renames the files back to their original names.
Information recovery after ransomware virus Faust (Phobos)
Another request for recovery in the form of a couple of SSD disks. Due to crooked system administrators, attackers using RDP access to the PC infected all files with an encryptor that changed the extension of the infected files to *.faust
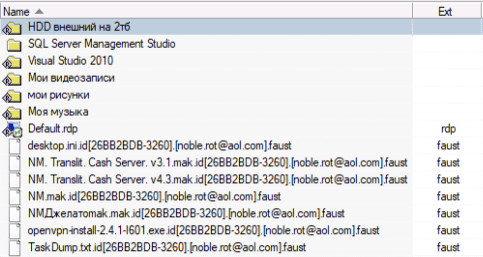
This is where the Faust virus got more creative. Small files are fully encrypted, but large files are worse. The usual 0x40000h offset of zeros,
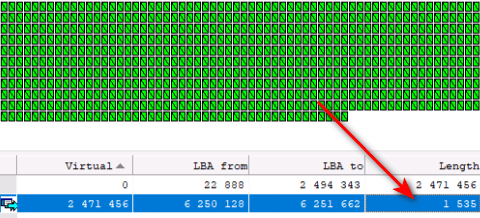
and to each file is added approximately the same number of sectors to the end of the file as a separate fragment filled with «white noise» with addressing to clusters in a common array at the beginning of the LBA space of the disk:
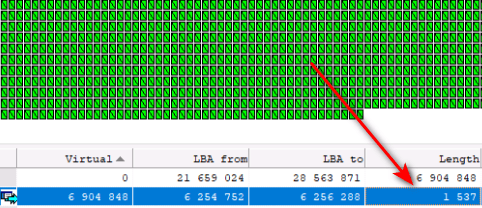
The size of the added «tail» exceeds the zeroed header by 4 times. In the presence of typical non-unique headers, recovery of user data after infection with the «faust» virus is not very difficult and all 1C user databases were successfully recovered by us.